FAQ What does the "dh key too small" SSL error means?
In updown.io or in your own manual tests (using curl, wget, some API clients, etc..) you may encouter one of the following error when trying to query your https website/API:
SSL_connect returned=1 errno=0 state: error dh key too small
curl: (35) error:141A318A:SSL routines:tls_process_ske_dhe:dh key too small
This error means your SSL setup is vulnerable because it supports small DH keys, and this is getting rejected by "recent" versions of OpenSSL.
This error means that the TLS client (OpenSSL in updown.io case) is refusing to connect because the DH (Diffie Hellman) keys size offered by your server are too small. The origin is a vulnerability in the protocol which caused TLS clients (like openssl) to increase security minimums to avoid them, your endpoint is now failing to connect because it doesn't respect these minimums, see: https://weakdh.org and https://stackoverflow.com/questions/61626206/what-could-cause-dh-key-too-small-error
SSLLabs is also mentioning this in their report for your websites, you'll see a line: "This server supports weak Diffie-Hellman (DH) key exchange parameters. Grade capped to B."
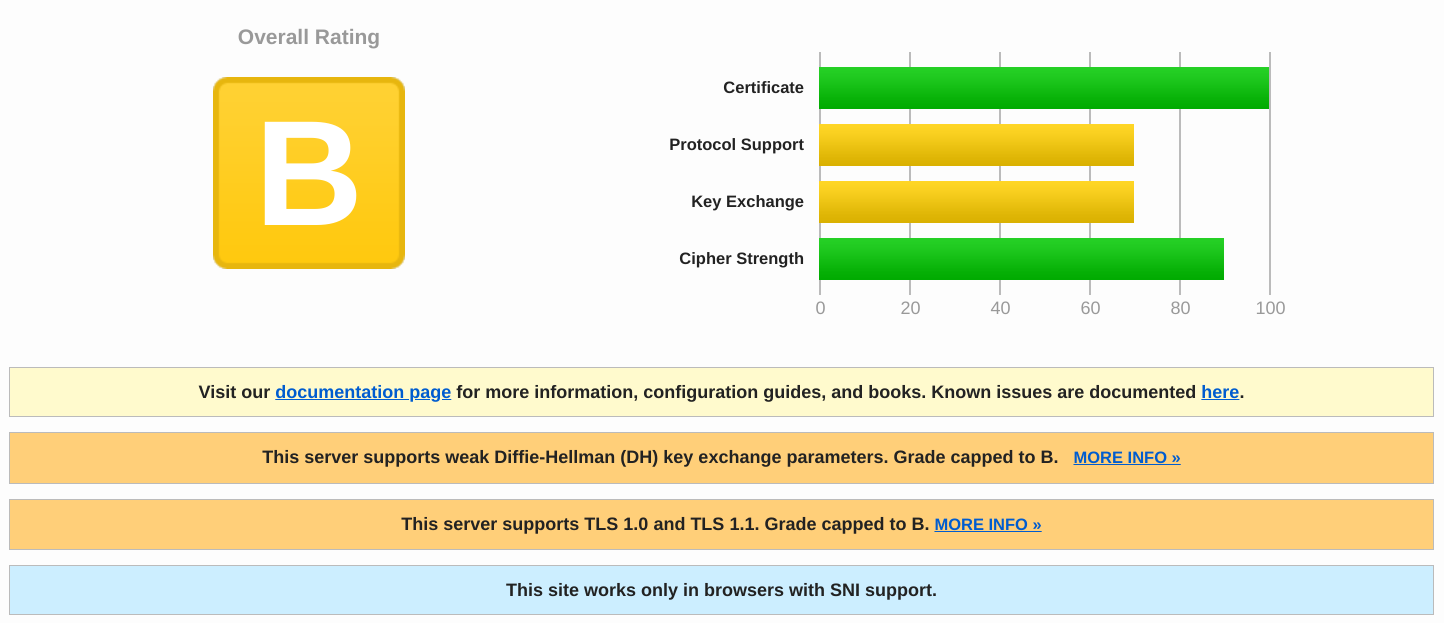
On a machine with an older version of OpenSSL which still accepts to connect, we can check the DH key size using the openssl command (1024 bits key in this example):
$ openssl s_client -connect $HOSTNAME:443 | grep "Server Temp Key"
# ...
Server Temp Key: DH, 1024 bits
(see https://www.openssl.org/blog/blog/2015/05/20/logjam-freak-upcoming-changes/)
The recommendation is to have at least 2048 bits.
This may not cause any problem in browsers at the moment (because they have a permissive implementation), but it may at some point, and it's already impacting stricter clients like curl or other programming HTTP APIs. That is why updown.io will not try to ignore this error (which is theoretically possible by lowering security settings for OpenSSL).
To resolve this you'll have to update and strengthen the TLS setup on your end. You may want to check the excellent https://ssl-config.mozilla.org/ if you need any help for this part.